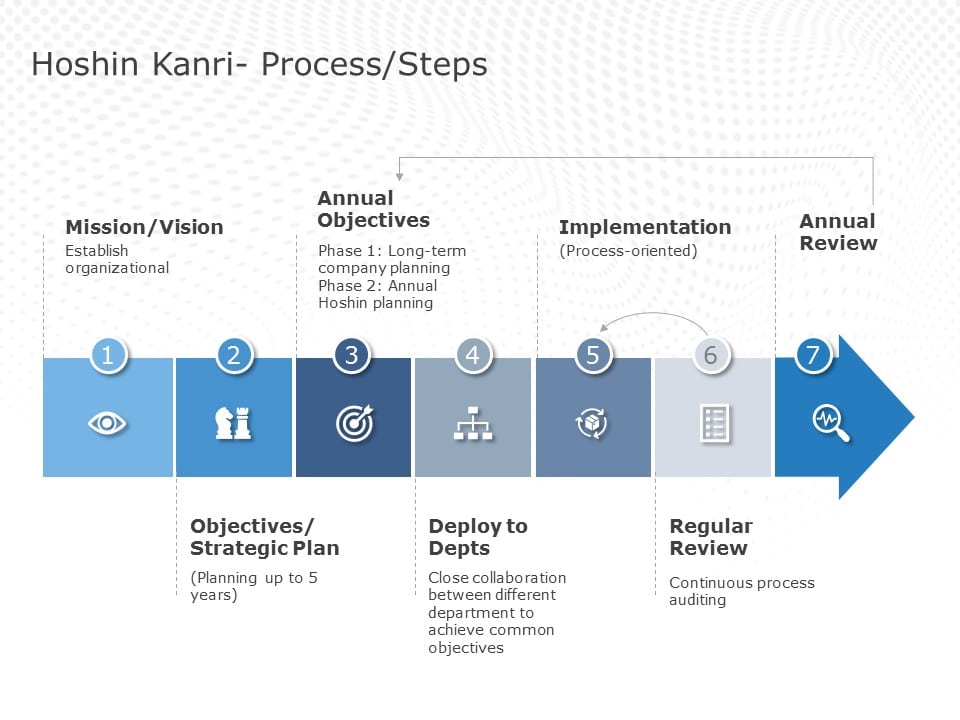
30+ threat model data flow diagram
Operational or infrastructure threat models OTMs are a specific type of data flow diagram visualising how the independent grouped and shared components communicate. Threat modeling uses traditional Data Flow Diagrams DFDs 8 with security-speciflc annotations to describe how data enters leaves and traverses the system.
1567 Editable Free Flow Chart Templates Slides For Powerpoint Presentations Slideuplift
In this longest episode of the worlds shortest threat modeling videos I introduce the five.

. Create a threat model using data-flow diagram elements. Data flow diagrams therefore are generated as a means of communicating this to the outside world those who are not threat modelers. In this step Data Flow Diagram should be divided in the context of Model View Controller MVC.
Data Flow Diagrams DFDs in the Threat Modeling Arena While DFDs are used to document the flow of data in out and around a system application. The analysis uses a Data Flow Diagram DFD to describe how. A threat model diagram is a visual form of threat model.
We start by deciding to focus on either what needs to be protected or who it. The resulting document is the threat model for the application. Process Flow Diagrams PFDs vs.
Include the right context for an. Visual Paradigm Online features an online threat model maker and a large variety of technical and. Module 8 Units Beginner Administrator Developer DevOps Engineer Security Engineer.
Threat modeling analyzes how an adversary might attack a system by supplying it with malicious data or interacting with it. Create threat models online. Use tools to draw your diagram If you dont like to manually draw your DFD.
The original intent of a data flow. Threat modeling is an effective technique to help you identify threats and ways to reduce or eliminate risk. User Login Data Flow Diagram for the College Library Website.
Automated threat modeling software using process flow diagrams allow defenders to approach their systems from the same vantage point as attackers architecturally. Data flow diagrams are very frequently used in threat modeling.

Navin Ramankutty Nramankutty Twitter

Code Quality Tools Tame Software Complexities Circuit Cellar

Threatmodeler About The Evolution Of Threat Modeling
What Is The Purpose Of Developing Dfds Quora

A Threshold Based Real Time Analysis In Early Detection Of Endpoint Anomalies Using Siem Expertise Sciencedirect
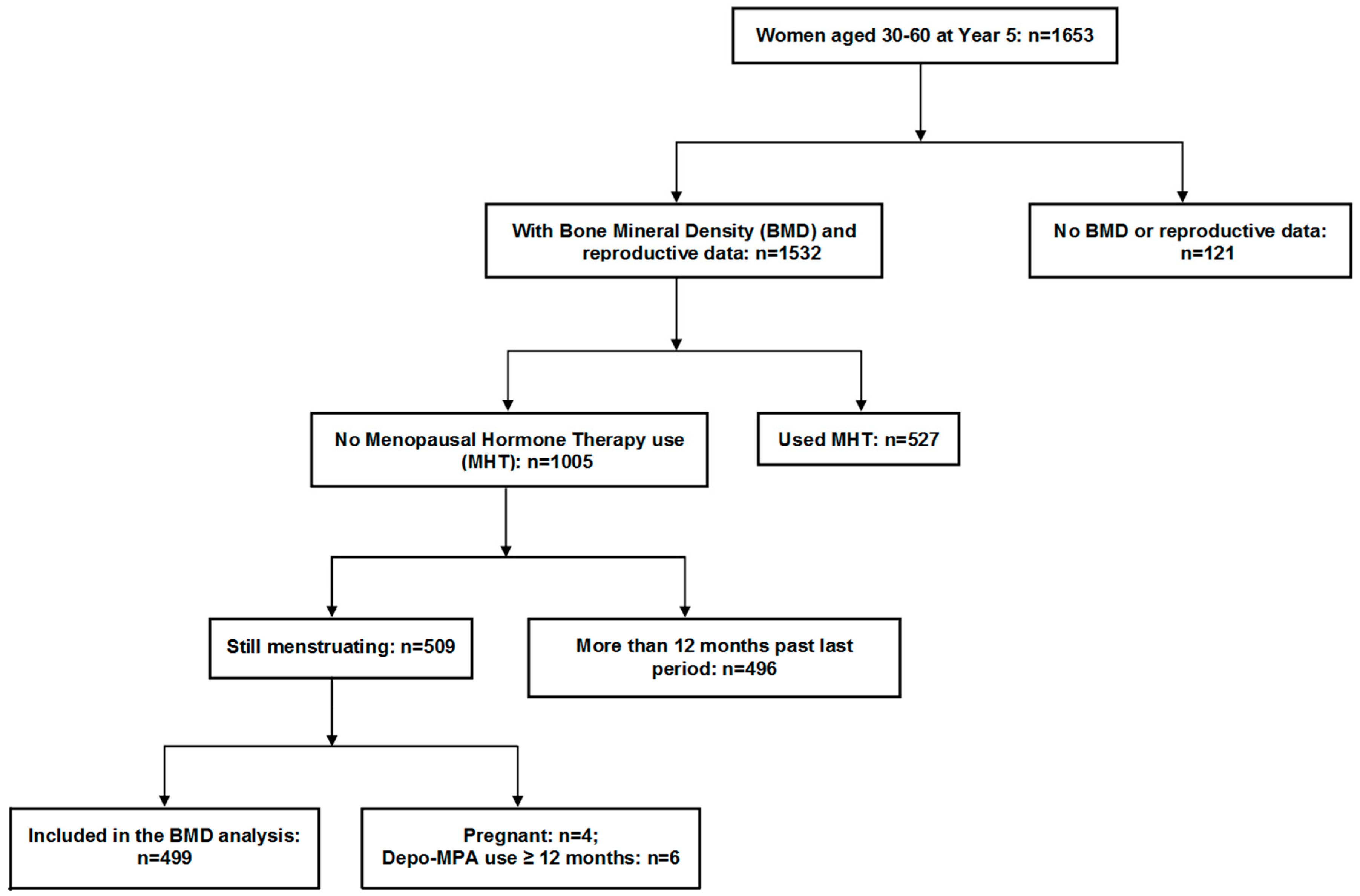
Ijerph Free Full Text Adult Premenopausal Bone Health Related To Reproductive Characteristics Population Based Data From The Canadian Multicentre Osteoporosis Study Camos Html
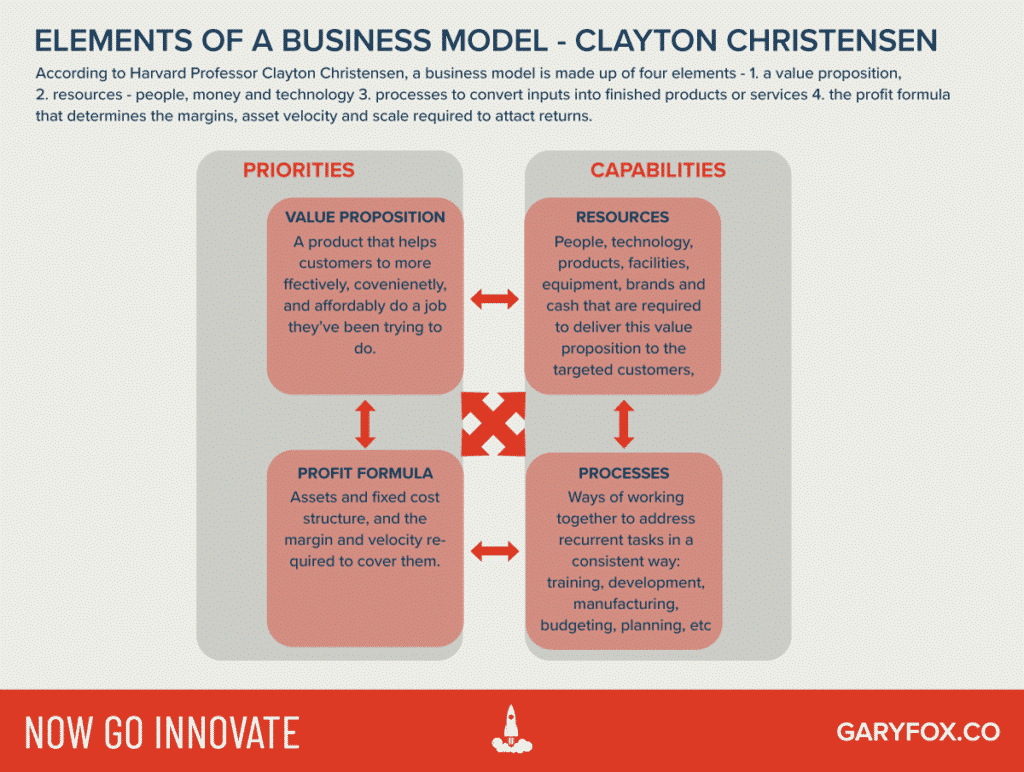
What Is A Business Model Definition Explanation 30 Examples

Graphing The Utility Grid On Aws Aws For Industries
100 Ai Use Cases Applications In 2022 In Depth Guide
![]()
Threatmodeler About The Evolution Of Threat Modeling
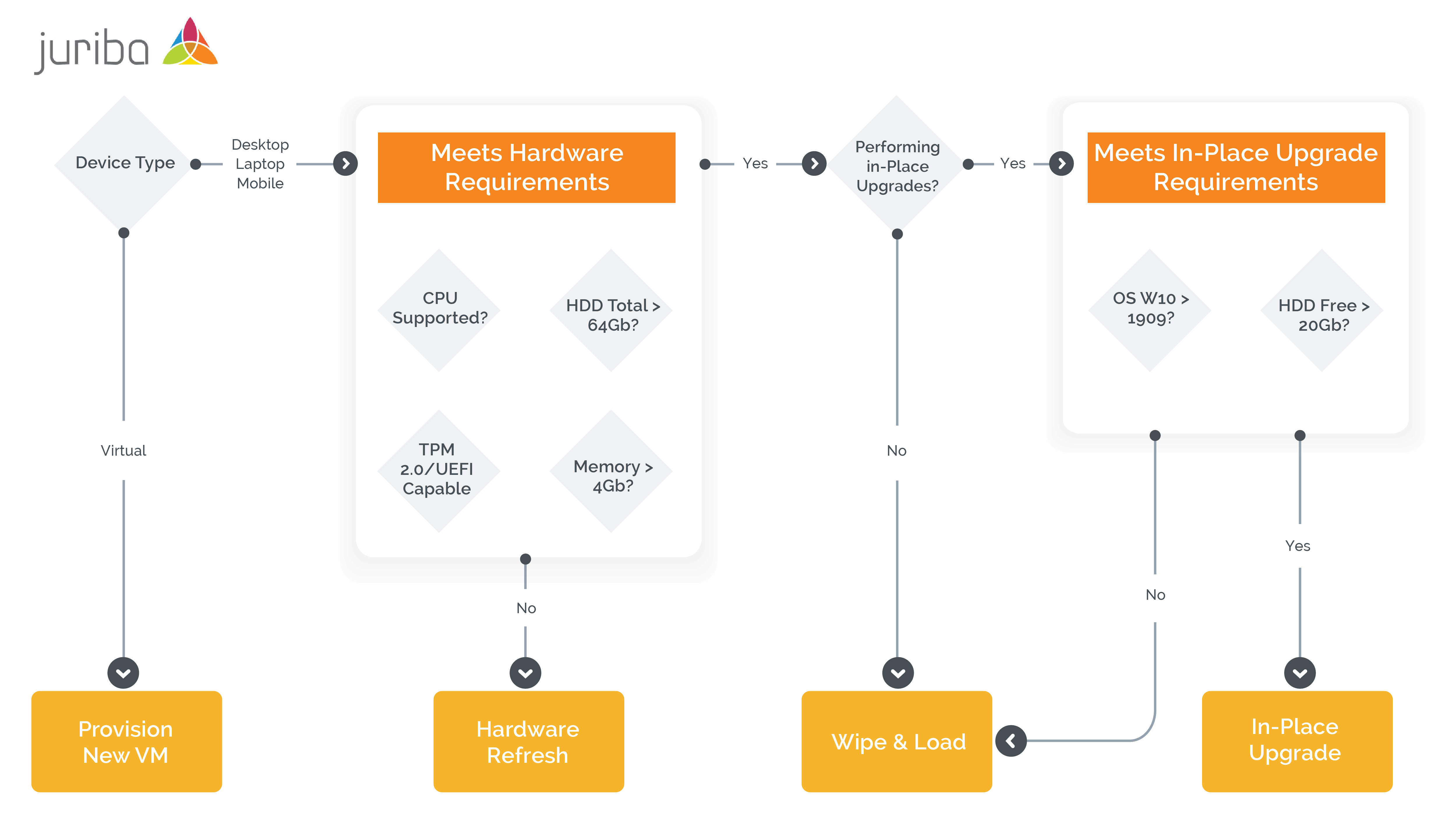
In Place Wipe Load Or Hardware Refresh How Windows 11 Hardware Requirements Will Determine Your Migration Strategy
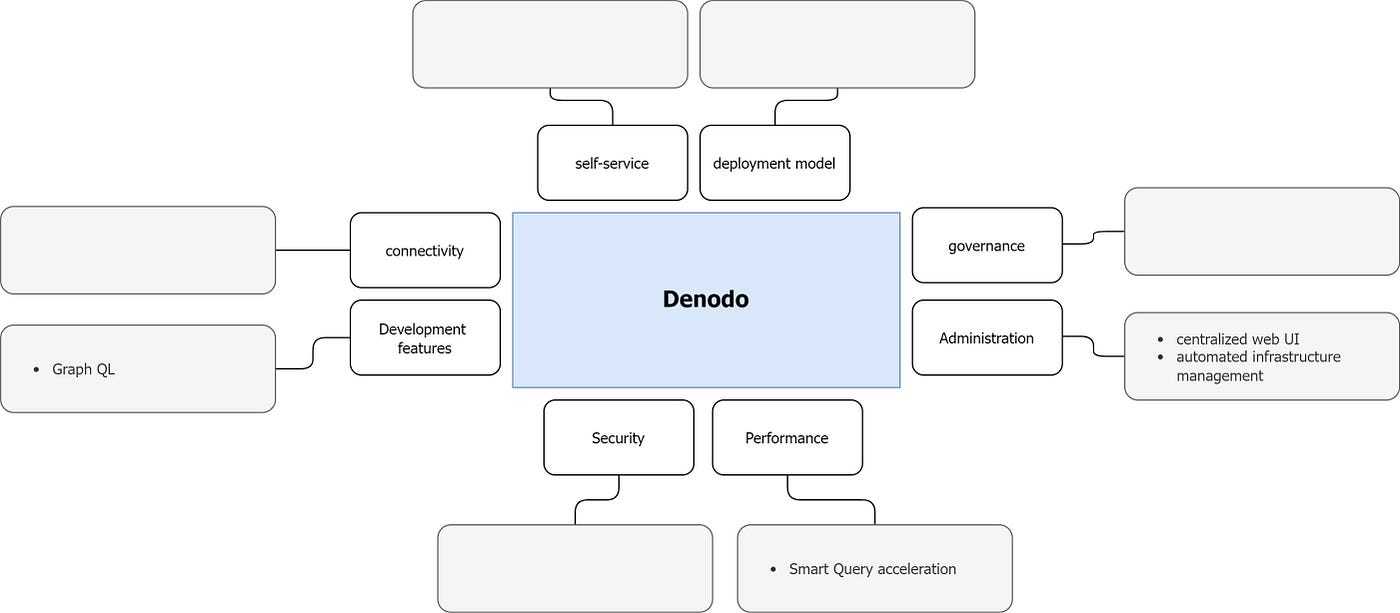
Data Virtualization Lets Review The Concept Of Data By Kanchan Tewary Medium
Top 35 Business Analyst Interview Questions And Answers 2022

Flowchart Symbols Flow Arrows Programming Process Flowchart Symbols With Labels Ad Arrows Programming Flow Flow Chart Symbols Process Flow Diagram

Graphing The Utility Grid On Aws Aws For Industries
Top 100 Power Bi Interview Questions And Answers Mostly Asked
Broad Whitefish Coregonus Nasus Isotopic Niches Stable Isotopes Reveal Diverse Foraging Strategies And Habitat Use In Arctic Alaska Plos One